 Minggu, 25 Mei 2025 (11:25)
Minggu, 25 Mei 2025 (11:25)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Anatomy of a Phishing Message (CSCAN | PlymUniInfoSec) (Cyber Security at the University of Plymouth) View |
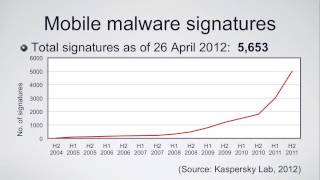 |
Mobile Malware (CSCAN | PlymUniInfoSec) (Cyber Security at the University of Plymouth) View |
 |
L-6.8: C-SCAN Algorithm in Disk scheduling with Example | Operating System (Gate Smashers) View |
 |
Development of unconventional ultrasonic methods at Fraunhofer IKTS NDT Lab (Fraunhofer IKTS) View |
 |
L-6.6: SCAN Algorithm in Disk scheduling with Example | Operating System (Gate Smashers) View |
 |
L-6.4: FCFS in Disk scheduling with Example | Operating System (Gate Smashers) View |
 |
L-6.5: SSTF in Disk scheduling with Example | Operating System (Gate Smashers) View |
 |
Write your first Python program (Hindi) (Varun Singh) View |
 |
UP POLICE COMPUTER OPERATOR PRACTICE SET | Network|Internet, Email Bcc Cc To|UP Police CO CLASSES-74 (EXAMINATION CLASSES) View |
 |
Disk Scheduling Algorithm | FCFS in Disk scheduling with Example | Disk management in OS (Edu Desire) View |